 Uber was hacked by an 18-year-old – here’s how he did it.
Uber was hacked by an 18-year-old – here’s how he did it.
On September 15th, 2022, Uber suffered an organization-wide cybersecurity breach by an 18-year-old hacker presumed to be working under the hacking group “Lapsus$”. Although Uber was able to confirm that no information was stolen, the hacker was able to gain access to many services and over a peta-byte of data on their Google Drive through social engineering alone. Although social engineering may seem easy to prevent, many companies underestimate how easy it is fall for, and this hack performed on Uber is a prime example of that.
Phishing for Employee Login Information:
Phishing, a social engineering hack where the victim is tricked into giving their information to the hacker, was the first step to gaining access to Uber’s system. After finding the employee’s contact information (speculated to be off the dark web), the hacker was able to message and trick the employee into entering their login information into a fake Uber website designed to phish information from users. This website sent all the employee’s login information directly to the hacker, where he was able to attempt logging in as an employee.
Bypassing Multi Factor Authentication:
Many businesses often attempt to secure their accounts using Multi Factor Authentication (also known as MFA). Multi Factor Authentication is the process of having an extra level of authentication to help ensure safety and security of login information. Although the idea of having an extra factor of authentication sounds safe, it can easily be bypassed by someone with good social engineering skills.
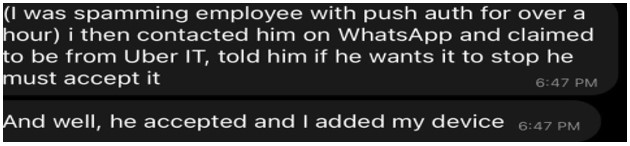
Hackers can combat MFA by using a technique called “MFA Fatigue” or “MFA push spam”. This is where the hacker repeatedly spams a device with Multi Factor Authentication prompts until the victim simply gets too annoyed and accepts/approves the request, which is exactly what happened with the Uber hack, where he was able to annoy and convince the employee into accepting the request.
Exploiting Hardcoded Information:
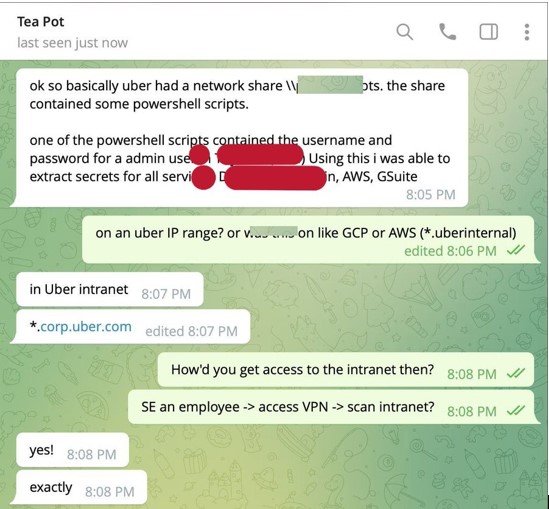
After logging in as an employee within Uber’s system, the hacker performed a scan across the company’s intranet (a local/restricted network) where he was able to find PowerShell script files, containing hardcoded (information that is directly written and saved into a file) login information for an admin account which he then used to access all services running for Uber. Not only did these scripts contain especially sensitive information, but they were also accessible to the entire company, meaning anyone who read this file could gain control over this account.
Preventative Measures for The Future:
Most of this Uber hack happened due to an employee not knowing better about social engineering. This, unfortunately, is quite common due to how underestimated social engineering attacks are in the world. To prevent further phishing or social engineering attacks, companies should stop assuming that their employees are “too smart” to fall for one of these attacks and implement the proper measures and education to prevent it.
Although MFA does help protect companies against stolen login information, a variety of implementations exist that can change how secure it is. Many companies, such as Uber, use MFA where a button must be pressed, or a code must be entered to confirm. As seen in this hack, this form of MFA can be very unsecure due to social engineering attacks. Companies should switch to FIDO2 MFA; Multi Factor Authentication requiring access to physicals keys as they’re the most secure form of MFA. Although they may be a lot less convenient than other forms of MFA, there is almost no way to bypass FIDO2 technology unless the key is physically stolen.
Companies should also make sure to never hardcode sensitive information such as admin credentials inside of files, and make sure that they’re properly secured to prevent the wrong people from accessing these files. Afterall, the hack at Uber happened because of how files were found containing admin login information, accessible to the whole company – which is almost as secure as no security at all! Talking




