 Details
Details
Sophos has released a hotfix for a critical vulnerability discovered in their firewall product by an anonymous researcher through a bug bounty program. Tracked as CVE-2022-1040, the flaw is categorized as an authentication bypass vulnerability, targeting the firewall’s Webadmin and User portals, allowing for remote code execution, and full control of the device by an attacker. The vulnerability has been issued a critical severity rating of 9.8 and affects versions 18.5.3 and prior.
Enable Automatic Hotfixes
Sophos have stated that customers who have the “Allow Automatic Installation of Hotfixes” feature active - which is enabled by default - will have already received the hotfix; however, due to the severity of this issue, a guide has been released to help customers confirm the change. To help aid in the process of enabling automatic hotfixes, see below for a walk through. After applying these changes, restart the device. This will prompt the system to check for available hotfixes. After that, a check will be performed every thirty minutes.
(Source)
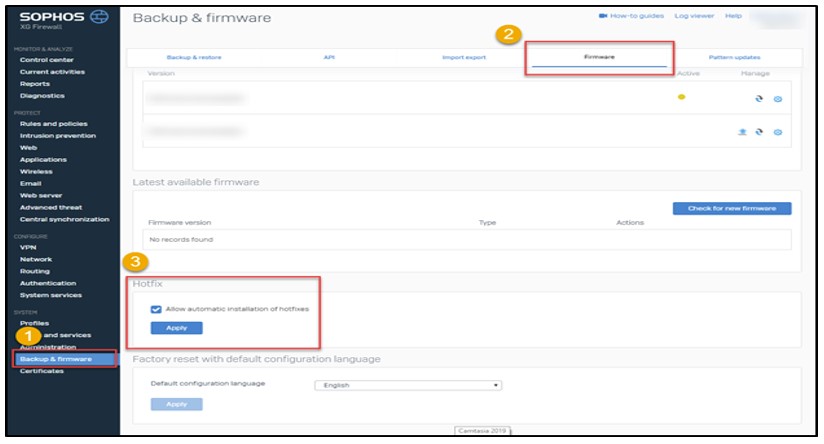
Hotfix Verification (Source)
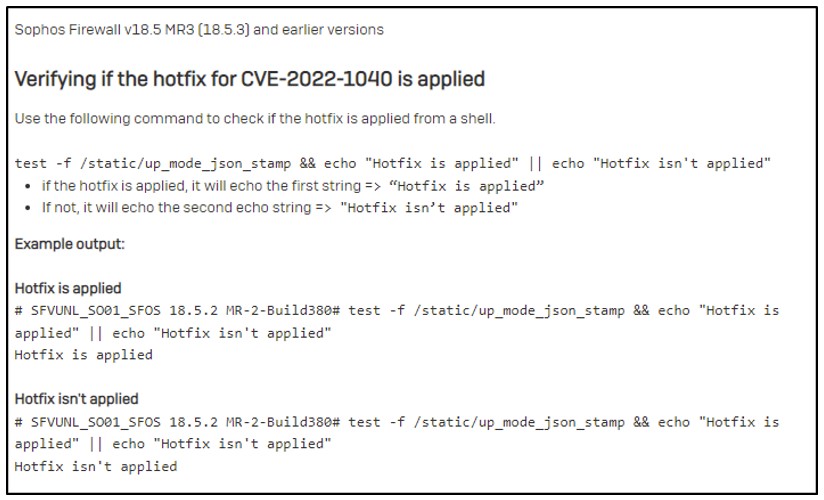
Remediation (source)
- Hotfixes for v17.0 MR10 EAL4+, v17.5 MR16 and MR17, v18.0 MR5(-1) and MR6, v18.5 MR1 and MR2, and v19.0 EAP published on March 23, 2022
- Hotfixes for unsupported EOL versions v17.5 MR12 through MR15, and v18.0 MR3 and MR4 published on March 23, 2022
- Hotfixes for unsupported EOL versions v17.5 MR12 through MR15, and v18.0 MR3 and MR4 published on March 23, 2022
- Hotfixes for v18.5 MR3 published on March 24, 2022
- Fix included in v19.0 GA and v18.5 MR4 (18.5.4)
- Users of older versions of Sophos Firewall are required to upgrade to receive the latest protections and this fix
Mitigation
Sophos also recommends minimizing the risk of attacks by disabling WAN access to the firewall’s User Portal and Webadmin interface in their guide to best practices, and instead suggests using a VPN and/or Sophos Central to improve the security of remote access and management.
Moving forward
If you are a user of Sophos Firewall products, it is critical that you check your device to ensure automatic hotfixes are enabled. In previous years, there has been a history of attacks on Sophos Firewalls from criminals who attempted to exploit zero-day vulnerabilities and steal usernames/passwords as well as install ransomware payloads on user's machines.
If you require assistance in navigating these changes, please reach out to us on social media, give us a call at (905)-731-9687 or send us a message here.




