
Enjoy our complete series from last years Cybersecurity Awareness Month. You can find all 8 episodes in this round-up! Learn to be cyber smart after watching the complete collection and reading our tips and tricks.
Cybersecurity Awareness Episode 1: Passwords
Are you or your co-workers guilty of any of these really bad password practices? Cybercriminals have much success in breaching your data and company accounts because many of us have really bad password hygiene. This short educational video will help you stay safe. After you watch the video, scroll down, and quiz yourself to see if you need to improve anywhere.
POP QUIZ: If you answer YES to any of these questions below - you have an unhealthy password practice that is putting you at risk!
- Do you use the same password for everything?
- Do you have multi-factor authentication disabled on websites that support it?
- Do you not know what a password manager is or do you not use one?
- Do you have a 'sheet of passwords' printed out anywhere?
- Do you ever say or think 'we are too small, nobody cares about our data'?
- Do you have a simple to guess dictionary word password?
- Do you use 'clever passwords' like 'Passw0rd123!' or 'letmein' ?
- Do you use 'easy to guess passwords' like the name of your spouse, child, pet or date of birth?
- Is your password 'hidden' under your keyboard or stuck to your screen with a post-it note?
Recommended Best Practices:
- Use Long, Random passwords for ALL work and personal accounts
- Do not use your work email for personal accounts
- Do no use the same password more than once on any given website
- Use a password manager
- Use Multi-Factor authentication everywhere that its available
Cybersecurity Awareness Episode 2: Data Handling
Share sensitive information only with those who are on a need to know basis. If the information you are sending is sensitive or contains PII encrypt the emails before sending. Not sure how to do this? We can help you. In this short video, we can see how sending sensitive information over email can quickly spiral out of control. Think before you send.
Cybersecurity Awareness Episode 3: Computer Theft
If your sensitive data is not encrypted or stored securely on a work server, computer theft represents a HUGE liability to you and your company. If your computer is lost or stolen make sure you call IT and have your logins changed ASAP, ideally the device is able to be wiped remotely as well. Here are 3 quick tips to remember:
- 1. If your machine is lost or stolen report the issue immediately
- 2. Remember to never turn off or install security tools
- 3. Never leave your computer unattended in public places
Cybersecurity Awareness Episode 4: Phishing and Ransomware
Phishing, we’ve heard of it, but what does it mean? In summary, it is a tool and method attackers use to try and coerce people into clicking on a malicious site or download, potentially leading to a security issue.
On the dark web, phishing is a very popular and effective way to try to steal data, lock data, delete data, gain access, or take over a computer. Phishing usually comes through email but can come via text message or other collaboration apps like Slack, Skype, or GroupMe.
Here are some signs of a phishing attempt. While the diagram below is email based, the same principles can be applied to the other communication methods mentioned above:
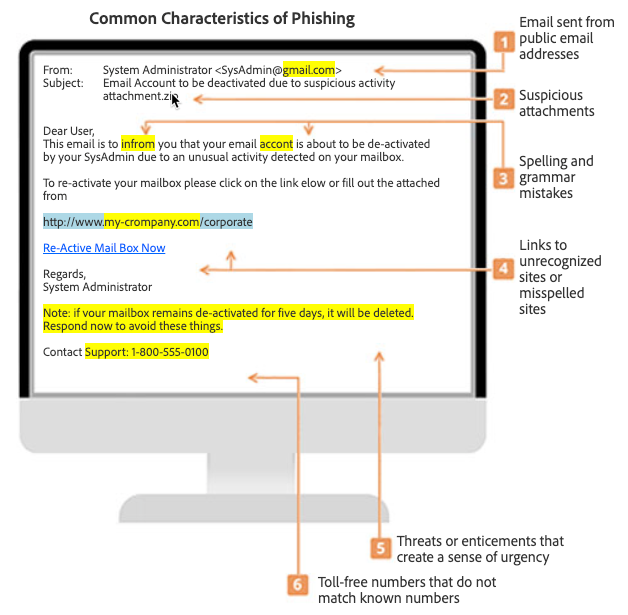
Phishing is usually obvious, and the above signs show prominently. However, some phishing attempts are tricky and it’s hard to spot a legitimate message from an illegitimate one. For example, amid the current crisis, many phishing attempts are using COVID-19 as their hook. Also, we’ll all recall, shortly after GDPR was passed there was a flurry of companies sending out updates to their privacy policy and emailing people about it. Well, attackers took advantage of this world-wide explosion of privacy policy updates and tricked many into clicking the links to “view or accept the new privacy policy”.
One of the best methods for protecting organizations and individuals against phishing is to report phishing attempts (Outlook > Report Phishing, Gmail > Report Spam). This helps the tool get smarter so that others don’t potentially get the same or similar emails.
As you’ll see on display in this newest security awareness video, ransomware is an especially dangerous consequence of falling for a phishing attempt. Ransomware is software that locks down data by encrypting it and won’t be unlocked through decryption until a ransom is paid. To protect yourself from ransomware:
- First, be wary of suspicious emails and look for the signs.
- Second, make sure your security software is up to date and running. It’ll help stop the ransomware in its tracks.
- Third, if ransomware is installed, then if you’ve backed up your data, you can ignore the threat and restore the data. Unfortunately, in many cases and especially for large enterprises, the cost of the ransom is significantly less than the cost to restore the data, even if it’s backed up. Therefore, the first and second layers of protection are critical.
Cybersecurity Awareness Episode 5: Removable Media
For those of us who have an altruistic desire to be good global citizens, when we find something that doesn’t belong to us our first inclination is to try and identify who it belongs to. Others, could have “selfish” intentions, and say “finders-keepers!”. In either of the above scenarios, the negative impact could be the same if the item that is found is removable media or a removable device that has malicious software embedded within – so finder beware.
Removable media and devices are portable hardware. The most common is a USB flash drive but other forms could be an external hard drive or SD card.
When it comes to cyber security best practices, removable media and devices must only be plugged or inserted into your computer if you trust/know the source. For example, if you found a USB flash drive in the grass near your office, there’s a chance it wasn’t dropped there by accident but planted there. A cyber attacker would try to social engineer someone into plugging the device into a computer. Whether the intention is to find out who it belongs to or keep it, the attacker wins and could successfully execute whatever malicious software might be pre-installed on the removable media or device.
Plugging or inserting only trusted removable media or devices into your computer is the best protection against this type of attack. Other preventive and detective measures would be:
- Install, run, and update anti-malware/anti-virus software on your computer.
- Do not enable auto-run features. These features automatically run whatever programs are installed on the media or device.
- Delete data on your computer, media, or device once its usefulness has expired. Redundancy of data results in more potential risks.
- Use a data blocker (AKA USB Condom)
- Use strong passwords and rotate them if you suspect they’ve been compromised.
As always, be extra careful with anything that does not come from sources you trust. That extra care is one of your best defenses against security issues.
Cybersecurity Awareness Episode 6: Vishing
The latest security awareness video covers “vishing” which is defined as the fraudulent practice of making phone calls or leaving voice messages purporting to be from reputable companies in order to trick individuals to reveal personal information, such as bank details and credit card numbers.
Recently I listed an item for sale on my local classifieds. Within seconds, I received several text messages and calls from seemingly interested buyers. I quickly noticed some of the messages had egregious misspellings and were from obscure, non-local numbers. I work in the cyber security industry and am aware that spam can occur when posting a phone number publicly. I disregarded the odd messages and odd phone numbers as scams – except for one.
One of the calls was from a local number. It was a legitimate buyer – or so I thought. After a few reasonable questions, they asked me to verify I was a legitimate seller. I wasn’t sure how I would prove that, but they made a suggestion I could verify I was legitimate by sending them the six-digit code just sent to me. Immediately my internal alarms triggered. I knew it was another scam attempt because a six-digit code wouldn’t prove anything. Nevertheless, sure enough, I received a text with a six-digit code to my cell. The message was from Google Voice with a warning to not provide the code to anyone.
As stated earlier, I work full-time in the cyber-security industry. I read about and teach others on how to recognize the signs. I knew this was a scam and blocked the number right away. But there are those who don’t know the signs and that’s who the scammers prey on.
Who are these scammers? Typically they are individuals looking for a pay-day or full-fledged hacking companies who even have an HR department. In the above example, if I had provided the six-digit code the individual could have been able to use my phone number to carry out illegal activities, and if they found enough information, could have the ability to compromise my Google account.
Think you can spot a vishing scam? Scammers get better every day and have more resources than ever before. Be vigilant, cautious, and skeptical. Even security professionals can fall for a scam if care isn’t taken. Check out the latest free security awareness episode on vishing as Sid – the ever-vigilant cybersecurity professional – let’s recognition go to his head and gets scammed.
Cybersecurity Awareness Episode 7: Internet Downloads
In high school it was a daily routine to download the latest and greatest music from platforms that shall remain unnamed. It was a futile effort because on multiple occasions I unintentionally downloaded malicious software which would crash the computer deleting all my music (and my parents tax info). Whoops!
The security threat of malicious downloads has widened in scope since my high school days. As internet users, we can download to our phones, laptops, desktops, tablets, etc. We can also download from emails, websites, instant messaging, text messages, etc. All it takes is a click or tap and, in some cases, we won’t even notice an application or file was downloaded and installed.
It’s enticing to download the latest free tool or software that makes our life easier without making a dent in our wallet. However, the return on investment (free) will likely net out to nothing significant. If a malicious file is downloaded, a computer could be out of commission for hours, days, or for good. Malicious software can spread to other parts of the network resulting hours, days, or even months of mitigation, so please use caution when downloading.
Only download reputable software from reputable sources. If you don’t know the source, or it looks suspicious, don’t risk it, head to the official source and go from there.
Cybersecurity Awareness Episode 8: Wi-Fi
Come on – let's admit it. We’ve all been in that desperate situation where we need Wi-Fi access but the only Wi-Fi around is “unsecured”. In other words, there is no lock symbol next to the familiar Wi-Fi symbol. It’s FREE, or so we think – as some economists put it..."there is no such thing as a free lunch".
Airports, cafes, community spaces, etc., don’t require a password to connect to the Wi-Fi. It is a great community service to offer free Wi-Fi, but users should know the guidelines and best practices when connecting to an unsecured Wi-Fi.
There are several ways an unsecured Wi-Fi connection can be a threat, but let’s focus on the top two basic scenarios:
1. Unsecured Wi-Fi set up as a legitimate public service.
2. Unsecured Wi-Fi set up to look like a legitimate public service.
Scenario 1 are your libraries, cafes, airports, etc. Everyone in that café is also using the same unsecure network. This means that with the right tools, which are easily accessible and don’t require a great deal of skill, adversaries can “sniff” for credentials being typed in or retrieve sensitive data. Zero-trust networks are the latest and greatest protections in this space, but VPN is an extra layer of protection. Try connecting to a hot spot on your phone, connect to your VPN service, and then connect to the free community Wi-Fi.
Scenario 2 are your Wi-Fi networks that are set up to trick users. These are especially devious because it takes less effort by adversaries to obtain the information your device is sending across the network. Even if you’re not doing anything on your device, by design, your applications send information the moment they are connected.
In either scenario above, you’ll want to avoid typing and entering credentials, especially for business or financial accounts, and especially if you’re not connected to a VPN. There are tools that can capture your keystrokes so be careful what you’re typing!




